Image source: https://image.slidesharecdn.com/nativevshybridapproach2-140728041957-phpapp01/95/native-vs-hybrid-approach-mobile-app-development-14-638.jpg?cb=1406521311
Native, HTML5, or Hybrid Information about Mobile Application Development Options.
Native, HTML5, or Hybrid: Information about Mobile Application Development Options.
Screens are small, apps are big and life as we know it is back on its head. In a world that is increasingly social and open, mobile apps play a crucial role and have shifted the focus from content on the web to apps on our mobile device. Mobile apps are no longer an option, they are a must. You need a mobile app, but where do you start? There are many factors in your mobile strategy, such as: These include, for example, the development capabilities of your team, the required device functionality, the importance of security, offline capability, interoperability, and so on. In the end, it's not just a question of what your app will do, but how you get it there.
Like Goldilocks, you may need to try a pair of beds that are too soft or too hard before you find the one that's just right. And sometimes there just is not a perfect choice. Each development scenario has its pros and cons, and these can be inline or disagree with your means. Unlike Goldilocks, there are no bears we are struggling with, and it is our intention that this article prevents you from burning your lips on hot oatmeal (well, figuratively).
While this article is generally about developing mobile apps, it is specifically designed for developers who want to build mobile apps that interact with Salesforce.com, Force.com, or Database.com. The Salesforce Mobile SDK currently supports the creation of three types of apps:
Native apps are specific to a specific mobile platform (iOS or Android) and use the development tools and language that each platform supports (for example, Xcode and Objective-C with iOS, Eclipse and Java with Android). Native apps look and deliver the best performance.
HTML5 apps use standard web technologies - usually HTML5, JavaScript, and CSS. This single-write approach, which can be run anywhere, creates cross-platform mobile applications that work across multiple devices. Although developers can create sophisticated apps using HTML5 and JavaScript alone, there are some important limitations at the time of writing, especially session management, secure offline storage, and access to native device features (camera, calendar, geolocation, etc.).
Hybrid apps allow embedding HTML5 apps in a thin native container, combining the best (and worst) elements of native and HTML5 apps.
Native mobile applications In short, native apps offer the best usability, the best features and the best mobile experience. There are a few things that you can only get with native apps: Multi-touch - double-tap, pinch spread and other connection UI gestures Fast Graphics API - The native platform gives you the fastest graphics, which is a big deal with a static screen with just a few elements or a lot of data a quick update.
Liquid animation - in the context of the fast graphics API is the ability to have fluid animation. This is especially important in games, highly interactive reports, or high-speed photo and sound conversion algorithms. Integrated Components - The device's camera, address book, geolocation, and other native features can be seamlessly integrated with mobile apps. Another important built-in component is encrypted memory, but more on that later. Ease of Use - The native platform is what people are used to. So if you add that familiarity with all the native features you expect, you'll have an app that's just easier to use.
Documentation - There are over 2500 books for iOS and Android development alone, with many more articles, blog posts, and detailed technical topics on sites like StackOverflow. Native apps are usually developed with an integrated development environment (IDE). IDEs provide tools for creating debugging, project management, version control, and other tools that professional developers need. While iOS and Android apps are developed using different IDEs and languages, there is a lot of parity in the development environments, and there is not much reason to be aware of the differences. Simply put, you are using the tools required by the device.
You need these tools because native apps are harder to develop. Likewise, the required level of experience is higher than in other development scenarios. They do not just cut and paste Objective-C and expect it to work. In fact, the technological know-how of your development team is an important consideration.
If you're a professional developer, you do not have to be sold on proven APIs and frameworks, painless special effects through established components or the benefits of having your code in one place. Let's face it, today an experienced native iOS or Android developer is a rock star and can make Rockstar claims.
While we got to know native apps from a development perspective, there is also the more important perspective: the end user. If you are looking for an app, you will find it in the shop. When you start the app, it will start immediately. Using the app gives you fast performance and a consistent platform look and feel. If your app requires an update, you will be notified. Native apps give you everything you expect from the company that built your device as if it were just meant to be. HTML5 Mobile Applications If you're new to mobile app development, you're late for the party.
For mobile web-based apps, however, we still celebrate like in 1999! Sure, browsers have gotten better in the last few years, but the underlying technology is not much different than if you feared the Y2K bug. But that can be a good thing. An HTML5 mobile app is basically a web page or series of web pages that work on a tiny screen. Therefore, HTML5 apps are device independent and can be opened with any modern mobile browser. And because your content is available on the web, it can be searched, which can be a big advantage depending on the app (for example, when shopping).
If you have experience in developing web apps, you will be taking HTML5 to the water like a duck. If you're new to web development, the technological bar is lower; It's easier to start here than with native or hybrid development. Unfortunately, every mobile device seems to have its own idea of what constitutes usable screen size and resolution, and therefore there is an added burden of testing on different devices.
The browser incompatibility is particularly common on Android devices, so the browser should be careful. An important part of the write-once-run-anywhere HTML5 method is that distribution and support is much easier than with native apps. Do you need to fix a bug or add features? Done and made available to all users. For a native app, there are longer development and testing cycles that the consumer typically needs to log into a store and download a new version to get the latest fix.
Over the past year, HTML5 has emerged as a very popular method for building mobile applications. Several UI frameworks are available to solve some of the most complex problems that developers do not want to reinvent. iScroll does a phenomenal job of emulating dynamic scrolling. JQuery Mobile and Sencha Touch provide sleek mobile components with hundreds, if not thousands, of plug-ins that range from merry-go-rounds to sophisticated controls. So, if HTML5 apps are easier to develop, easier to support, and able to reach the largest possible number of devices, where are these apps losing importance? We have already reviewed the main benefits of native development. We just want to repeat that you can not access native features on the device.
Users will not be familiar with the native look and feel or be able to use compound gestures that they are familiar with. But progress is being made on all fronts, and more and more features are always supported by browsers. The latest batch of browsers supports hardware-accelerated CSS3 animation features, offering smooth movements for slidable panels and transitions between screens, but even these can not match the performance and flexibility of native apps.
Today, it's just not possible to capture multi-touch input events (detect when there's more than one finger on the screen) or create path-style elegance with spin-out buttons and photos that float and then fall into place. Especially for mobile companies, however, there are significant limitations regarding offline storage and security. While you can implement offline features by caching files on the device, this is not a good solution. Although the underlying database may be encrypted, it is not as well-segmented as native keychain encryption, which protects every app with a developer's certificate.
When launching a web application with authentication from the desktop, users must enter their credentials each time the app is sent to the background. This is a lousy experience for the user. In general, implementing even trivial security measures on a native platform can be complex tasks for a mobile web developer. So if security is paramount, it can be the deciding factor on which mobile technology you choose.
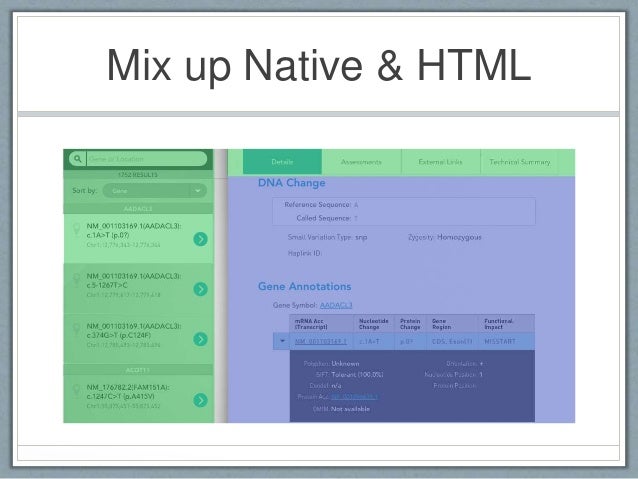
Hybrid Mobile Applications Hybrid development combines the best (or worst) of the native and HTML5 worlds. We define hybrid as a Web application that consists primarily of HTML5 and JavaScript and then embedded in a thin native container that provides access to native platform features. PhoneGap is an example of the most popular container for creating hybrid mobile apps. In most cases, hybrid apps offer the best of both worlds. Existing web developers who have become gurus in optimizing JavaScript, using CSS to create beautiful layouts, and writing HTML code that works on any platform can now create sophisticated mobile applications that do not sacrifice native capabilities.
In some circumstances, native developers can write plug-ins for tasks such as image processing, but in such cases the devil is in the details. On iOS, the embedded web browser or UIWebView is not the same as the Safari browser. While the differences are small, they can cause debugging issues. For this reason, it pays to invest in popular frameworks that have taken all constraints into account. You know that native apps are installed on the device while HTML5 apps are on a web server.
So you'll wonder if hybrid apps store their files on the device or on a server. Yes. In fact, there are two ways to implement a hybrid app. Local - You can package HTML and JavaScript code in the mobile application binary file, similar to a native application. In this scenario, you use REST APIs to move data back and forth between the device and the cloud. Server - Alternatively, you can implement the full Web application from the server (with optional caching for better performance) by simply using the container as a thin shell over UIWebview.
Netflix has a really cool app that uses the same code base to run the UI on all devices: tablets, phones, smart TVs, DVD players, refrigerators, and cars. While most people have no idea and do not care how the app is implemented, you are interested in knowing that they can change the interface on the fly or perform A / B testing to determine the best user interactions. The core of decoding and streaming video are delegated to the native level for optimal performance.
So it's a fast, seemingly native app that truly offers the best of both worlds. Conclusion Mobile development is a constantly moving goal. Every six months, there is a new mobile operating system with unique features that can only be accessed with native APIs. The containers soon bring them to hybrid apps, with the Web making huge leaps every few years. Based on current technology, one of the scenarios described in this article will meet your needs.